Understanding Decentralization: A Guide to 10 Top Blockchain Consensus Methods
Karolina Kondrak
8 min of reading
Blockchain technology is built on the concept of decentralization. In a traditional centralized system, a single entity, such as a government or a company, has control over the system. However, in a decentralized system like blockchain, there is no single central authority that is in control, yet the transactions in the Blockchain are considered to be completely secure and fully verified. How is this achieved?
This is where the consensus methods come in.
There are several of them, each having their own advantages and disadvantages and significant impact on its security, scalability, and energy efficiency. Choosing the right consensus method is an important consideration for developers and users.
In this blog post, we will discuss some of the most common, and those less widespread consensus methods used in blockchain technology.
What is decentralization?
Blockchain technology is a decentralized system. It is controlled by a network of users, as opposed to a single controlling authority, and any changes made to the system must be agreed upon by the network.
Consensus methods are used to ensure that all nodes in a blockchain network agree on the state of the network. They are the mechanism by which nodes in the network reach agreement on the validity of transactions and the current state of the ledger.
This allows for secure and transparent transactions without the intermediaries through the consensus among all participants in the network.
What is a consensus?
In the context of blockchain, consensus refers to the process of agreeing on a single version of the truth. Consensus algorithms ensure that all nodes in the network agree on the same set of transactions and the same state of the ledger.
Why is consensus important?
Consensus is critical in a blockchain network for several reasons:
-
Security. Consensus algorithms ensure that all nodes agree on the same set of transactions and that the transactions are valid. This prevents fraud and other malicious activities.
-
Decentralization. Consensus algorithms allow for decentralized decision-making. No single entity controls the network, making it more resilient to attacks and failures.
- Transparency. Consensus algorithms ensure that all nodes have access to the same information. This promotes transparency and reduces the risk of errors and disputes.
The overview of consensus methods
1. Proof of Work (PoW)
Proof of Work is the consensus method used in the Bitcoin network. In PoW, nodes compete to solve a complex mathematical puzzle. The first node to solve the puzzle gets to add a new block to the blockchain and receive a reward in the form of cryptocurrency. The solution to the puzzle is called a hash, and it takes a significant amount of computing power to find the solution. This process is called mining.
The main disadvantage of PoW is its high demand for electricity and computing power. This makes it rather slow and expensive to use. It is also not the most environmentally friendly method.
In terms of security, on the one hand PoW is vulnerable to a 51% attack. This means that if a user or a group of them seize more than 50% of the total mining capacity, they will have the ability to make changes to a particular block.
On the other hand, the high cost of mining also makes attacks costly, hence this method offers a relatively high level of security. It is also a protocol that is proven on a large scale, due to its age and widespread use. Under Bitcoin, it has safely and securely stored more than $1 trillion.
2. Proof of Stake (PoS)
Proof of Stake is a consensus method used in many newer blockchain networks. In PoS, nodes that can approve transactions are selected based on various random attributes, such as age or the number of cryptocurrencies held at a given address. In order to participate in the chain-building process, users must deposit, or block, a certain number of coins (this is known as staking). Nodes with more coins in this case will have a higher chance of being selected for transaction approval. The reward for approving transactions is a percentage of the transaction fees, and in some cases of cryptocurrencies, also a certain unit of it.
PoS is an algorithm that is relatively easy to adapt to specific usage needs. Therefore, there are many consensus mechanisms in various blockchains based on this algorithm (some of which are described below).
Regarding the advantages of PoS, it is certainly a faster and more energy-efficient method than PoW: it does not require users to solve complex mathematical puzzles. It's also more scalable, since it doesn't rely as much on powerful, physical machines for consensus.
PoS is often seen as a more decentralized mechanism and more easily accessible to a wider range of stakeholders. But here, too, there is a risk of monopolizing the network: nodes with more cryptocurrencies potentially have more leverage and influence in the network. Some of the Proof of Stake-based cryptocurrencies have no limits on the amounts staked by individual validators.
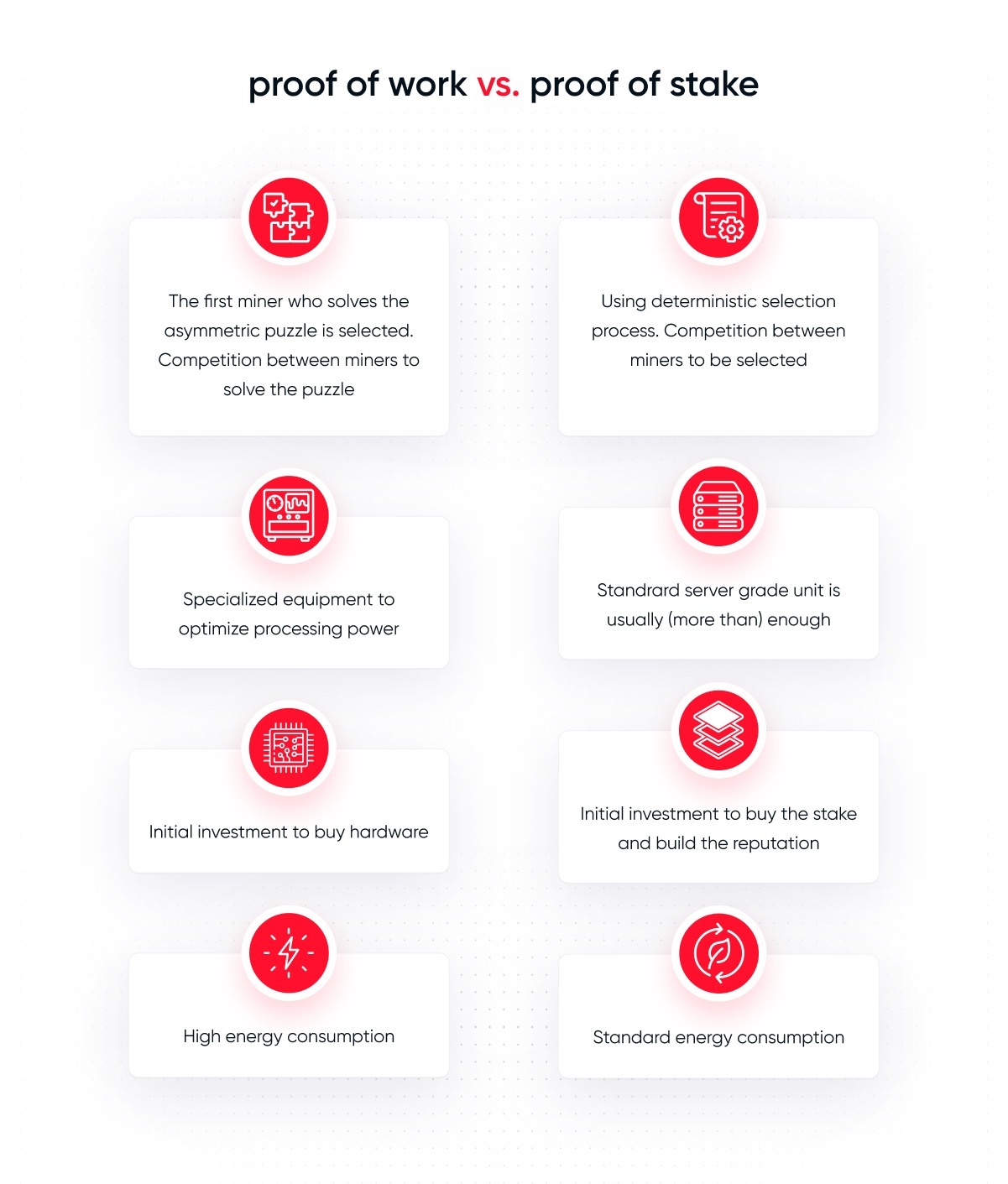
Proof of Work and Proof of Stake: a brief comparison.
3. Delegated Proof of Stake (DPoS)
Delegated Proof of Stake is a variation of PoS used in some blockchain networks. In DPoS, users, stakeholders holding a specific cryptocurrency, select validators to whom they entrust the pledged coins. Validators, also known as delegates, are responsible for validating transactions. Delegates receive a reward for their work.
This method is faster and more efficient than PoS and PoW because it eliminates the need for all nodes to validate transactions. It also does not require nodes to solve complex mathematical problems. DPoS is more scalable because it is able to process more transactions per second (TPS). The entry threshold is relatively low, and for this reason DPoS is seen as one of the most democratic and decentralized consensus algorithms.
In terms of risks, DPoS relies on a smaller group of nodes known as delegates, or witnesses, to approve transactions, which can increase the potential for centralization. The algorithm is susceptible to malicious attacks such as the Sybil, where control over a significant number of nodes can be gained, potentially allowing the network to be manipulated.
4. Byzantine Fault Tolerance (BFT)
Practical Byzantine Fault Tolerance is a consensus method that links to the issue of the problem of Byzantine generals from game theory, where generals are trying to establish a common, coordinated action and are faced with the problem of effective communication.
The concept is that in order not to fail, it is crucial for different parties to make the same decision, whether the decision is to attack or withdraw.
In PBFT, nodes exchange messages and vote on the validity of a transaction. The algorithm goes through several phases, including a request phase, a pre- preparation phase, a preparation phase, a commitment phase and a response phase. During each phase, the nodes communicate with each other and try to reach an agreement on the validity of the transaction. If a node fails to act or acts to the detriment of the system, the other nodes can identify it and rule it out of the consensus process.
This algorithm offers many advantages: a high level of fault tolerance, even in the presence of faulty or malicious nodes. The method is faster and more efficient than PoW and PoS, as it does not require solving sophisticated calculations. PBFT can be used in authorized blockchain networks where nodes are known and trusted, making it suitable for enterprise use cases.
PBFT can be resource-intensive, requiring a lot of network load to ensure agreement between nodes. On the other hand, it can be troublesome in terms of scalability, due to the high volume of communication. It is also not suitable for large public blockchain networks, where nodes may not be known or trusted.
5. Proof of Authority (PoA)
Proof of Authority (PoA) is a consensus algorithm used in some blockchain networks in which block validation is performed by a select group of nodes known as validators. They are identified and authorized by network administrators, and their identities are publicly known.
Unlike other consensus mechanisms, such as Proof of Work (PoW) or Proof of Stake (PoS), PoA does not require nodes to solve complex mathematical problems or hold large amounts of cryptocurrency to validate transactions. Instead, the reputation and credibility of the approvers acts as a safeguard against malicious activity on the network.
Other Proofs
What about other "proof of" algorithms used in cryptocurrencies and blockchain systems? While not all of them are as widely used or considered as secure as their more popular cousins PoW and PoS, they are worth keeping an eye on. This is because they are evidence that research and development in blockchain and cryptocurrencies is ongoing, and they may become more important in the future as new scenarios and use cases emerge.
6. Proof of Burn (PoB)
This is a consensus algorithm that involves destroying ("burning") cryptocurrency to prove that the node is committed to the network. The more cryptocurrency a node burns, the more likely it is to be selected to validate transactions and create new blocks.
7. Proof of Capacity (PoC)
In this algorithm, nodes prove their commitment to the network by allocating a portion of their hard drive space to store blockchain data.
8. Proof of Elapsed Time (PoET)
This consensus algorithm is used in some enterprise blockchain applications and requires nodes to wait a randomly determined amount of time before being allowed to validate transactions and create new blocks.
9. Proof of Importance (PoI)
This is a consensus algorithm used in the NEM cryptocurrency network, which takes into account a node's "importance" based on factors such as the amount of cryptocurrency held, the number of transactions processed, and the node's reputation within the network.
10. Proof of Reputation (PoR)
This algorithm is used in some blockchain applications to ensure that only nodes with a good reputation within the network are allowed to validate transactions and create new blocks.
Conclusion
In the world of blockchain technology, consensus mechanisms are the backbone of secure and decentralized systems. These mechanisms are responsible for ensuring that all nodes in the network agree on the same set of transactions and the current state of the ledger. The selection of a consensus algorithm is a technical decision that can have significant implications for the network's performance, energy consumption, and security. Therefore, it is essential for developers to conduct thorough evaluations and choose a consensus method that fits their network's specific requirements.
Consensus is a critical component of blockchain technology. Overall, each method has its own advantages and disadvantages, and choosing the right consensus method can have a significant impact on its security, scalability, and energy efficiency.


